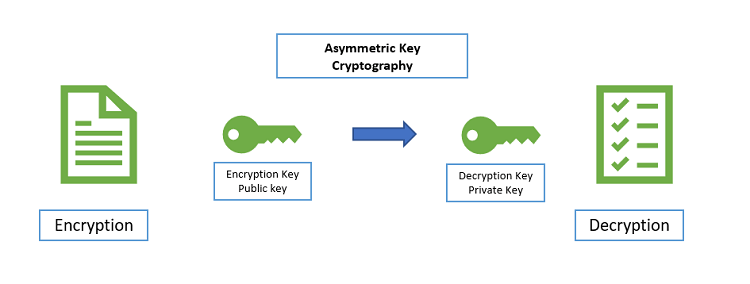
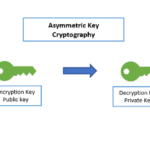
- In this everyone(nodes) will have 2 keys
- Private key
- Public key
- To encrypt and decrypt a message we shall need both the keys i.e.;
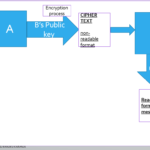
- A wants to send a message to B. Both A and B have private and public keys. So A will ask for B’s Public key and encrypt the message using B’s public key. The message then becomes a non readable format (cipher text). Everyone can see the message but to one can decrypt it, Only B can, using their private key.
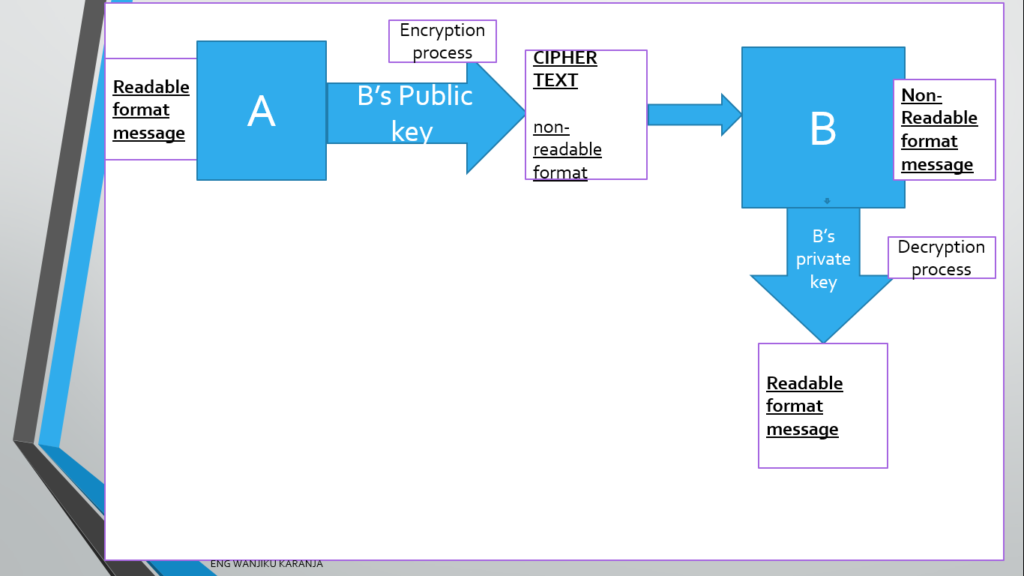
- The above has a drawback. In that A only uses B’s public key to encrypt the message, we then lack As footprints on the blockchain to ascertain that they are the one who sent the message. This then brings the issue of lack non-repudiation and authenticity. Lets now see how we can achieve non-repudiation and authentication.
ENG WANJIKU
Views: 13