TOPIC 10: DIGITAL SIGNATURES
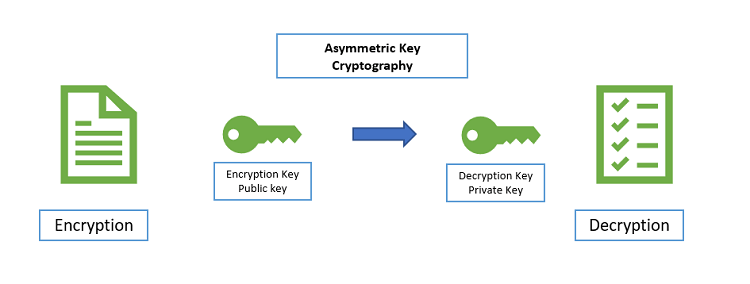
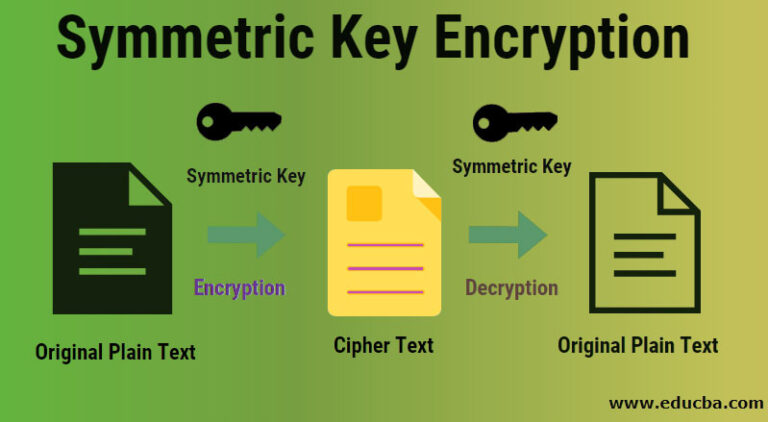
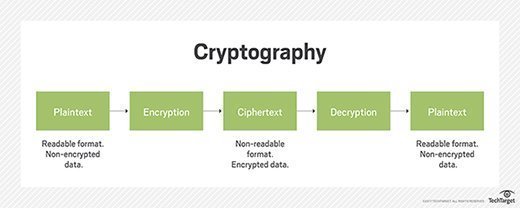
To achieve this we do DOUBLE AUTHENTICATION That is, if A wants to send a message to B, A will first encrypt the message using their private key which is inaccessible to the public thus acting as a digital signature The second encryption is done using B’s public key For B to get the readable […]
TOPIC 10: DIGITAL SIGNATURES Read More »