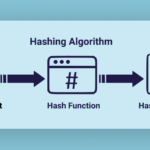
- Hash function is a mathematical function which takes arbitrary length of numerical data and converts it into a fixed length numerical data
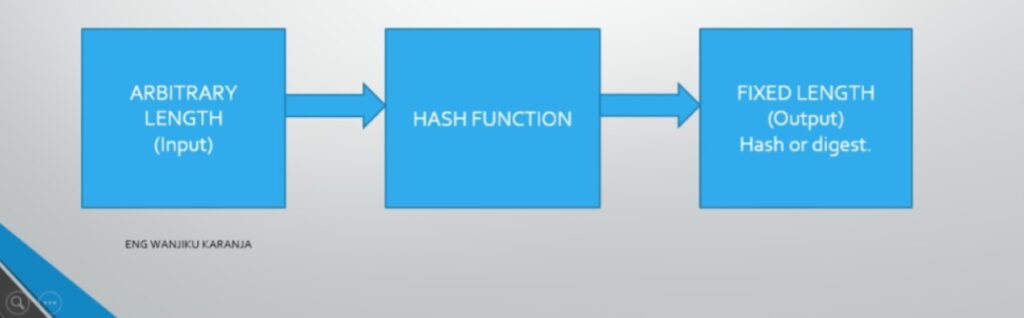
Depending on what algorithm the hash function will use i.e. SHA or MESSAGE DIGEST, We shall get a different set or length on the output.
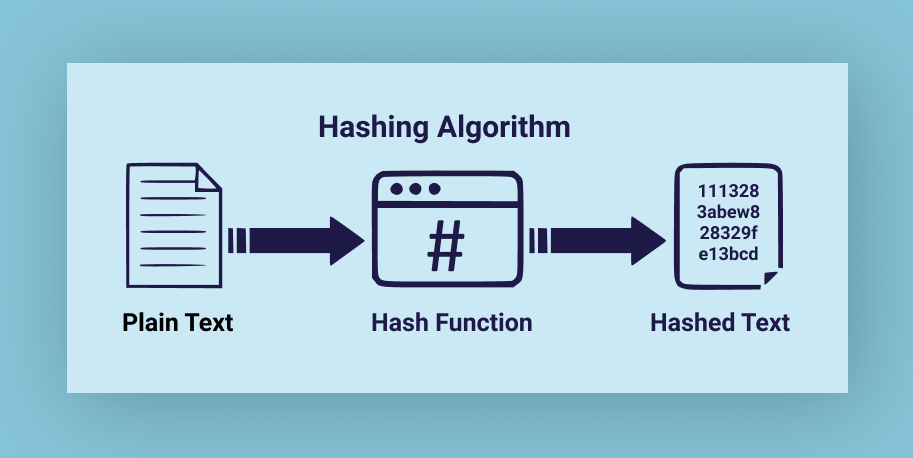
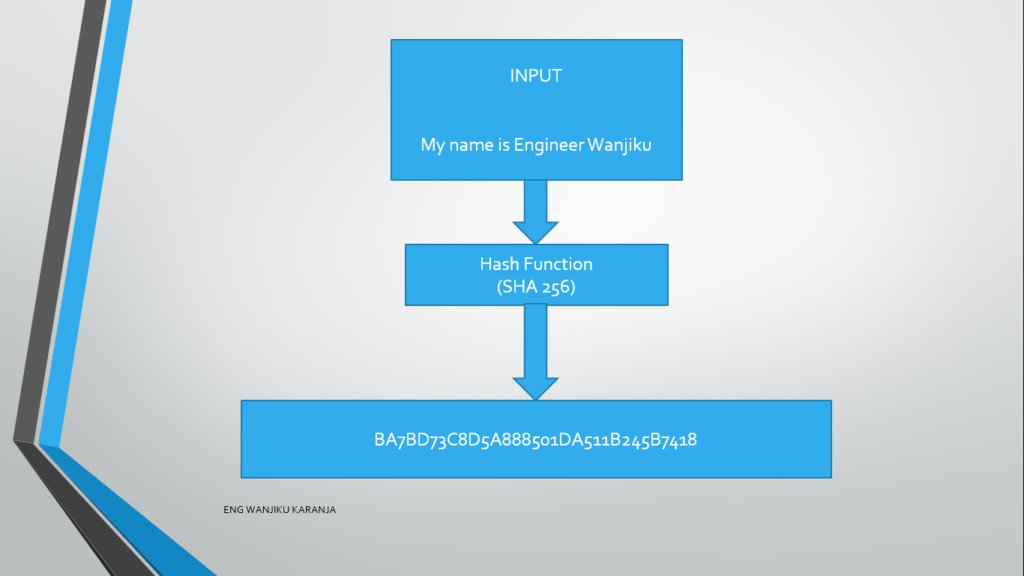
Example if you take my name and type as your input “My name Engineer Wanjiku”, you will get a hash value(output).
The amazing thing is for each algorithm used, the hash value output will be the same for the same input.
Below is a detailed example:
•If you have a small change in your Input i.e. in this case “My Name is Engineer Wanjiku”, the hash function output will change. Even a slight change like having the word name in capital N will change the whole output value.
NB: Reverse is NOT possible i.e. you cannot take the hash value to give you the input.
Its possible to convert data into hash ,but hash to data is impossible
This hash values are what is used in the blockchain.
There are different algorithm available for converting data to hash value.
MD– Message digest (MD2,MD3, MD4,MD5,MD6)
SHA– Secure Hash Algorithm ( SHA0,SHA1,SHA2). Built by NSA(National Security Algorithm)
•The popular SHA, IS SHA2. SHA2 has 2 popular versions
SHA2 256
SHA2 512
SHA 256 – means that the output will have 256 bits. SHA 512, the output will be 512 bits.
ADVANTAGES OF USING HASHING IN AN EXAMPLE
•Assuming you want to download UBUNTU from U-torrent. And what if the set up that you are downloading from U- torrent is malicious and has malware?
How do you verify that the set up you are downloading is official?
Click on the official website for Ubuntu and get the HASH value and generate the HASH value then you can compare the values and if they match then this confirms that the set up you are downloading is legit
Because if a hacker changes anything, it will change the entire HASH value.
ENG WANJIKU
Views: 14