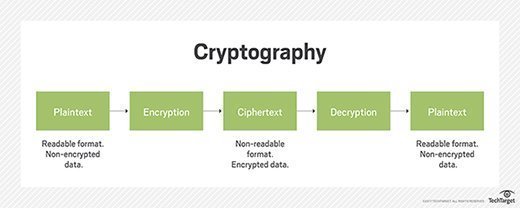
Crypt – hidden/ secret
Graphy- writing
- Therefore, Cryptography is the practice of protecting information by transforming it into a secure format
- This means when sending a message you have to convert it to a way that someone else will not be able to read it but the intended receiver cab read it
Peer to peer network has been in existence from long ago, if you can remember the music sharing platform NAPSTER and TORRENT , they used peer to peer network
But our major concerns of peer to peer network(P2P) were;
- Confidentiality
- Integrity
- Non- Repudiation
- Authentication
CONFIDENTIALITY
Lets say A sends a message to B. A simple message that is confidential i.e. Bank details, and since the blockchain is open source, this details can be accessed by anyone i.e. person C . Now this confidentiality factor is what we want to achieve with cryptography
INTEGRITY
Lets say A wants to send a message to B i.e. “Lets meet at 6pm ”. But since the blockchain is open source, Person C can edit this information to lets meet at 5pm . So that the data received by B is not what A initially sent. Now this integrity factor is what we want to achieve with cryptography
NON-REPUDIATION
This simply means you cannot deny not doing something on the blockchain. Lets say A sends a message to B “Lets meet at 6pm ”. B shows up and A claims not to have sent the message. This is what we do not want. There should be a proof that A did send that message. Now this non-repudiation factor is what we want to achieve with cryptography
AUTHENTICATION
Lets say B has received a message “Lets meet at 6pm ” and the message was sent by A. What is the guarantee that A sent the message and not C?? Since the Blockchain is open source and can be accessed by anyone hiding behind A’s identity? Now this authentication factor is what we want to achieve with cryptography
How do we solve the above concerns??
Lets us first see how we can achieve confidentiality and integrity.
- In this we use the concept of encryption and decryption . This brings forth two types of cryptography.
- Symmetric key cryptography
- Asymmetric key cryptography
We shall look at them individually in the next chapter.
ENG WANJIKU
Views: 22